Cyber Protection represents an all-in-one cyber protection solution that integrates backup and recovery, disaster recovery, malware prevention, security controls, remote assistance, monitoring, and reporting.
It protects your entire business and businesses of your customers through layered protection approach, an innovative combination of proactive, active, and reactive data protection technologies:
- Proactive actions, such as vulnerability assessment/patch management, predictive analysis of hard drive health based on machine learning technologies, allow you to prevent any threats to your machines.
- Active actions, such as protection against malware, self-protection, allow you to detect threats.
- Reactive actions, such as backup and recovery (on-premises and cloud), disaster recovery (on-premises and cloud), allow you to respond to any failures.
Cyber Protection provides you with one protection agent, one service console that is easy to manage, and one protection plan that covers all security and data protection aspects.
Key functionality
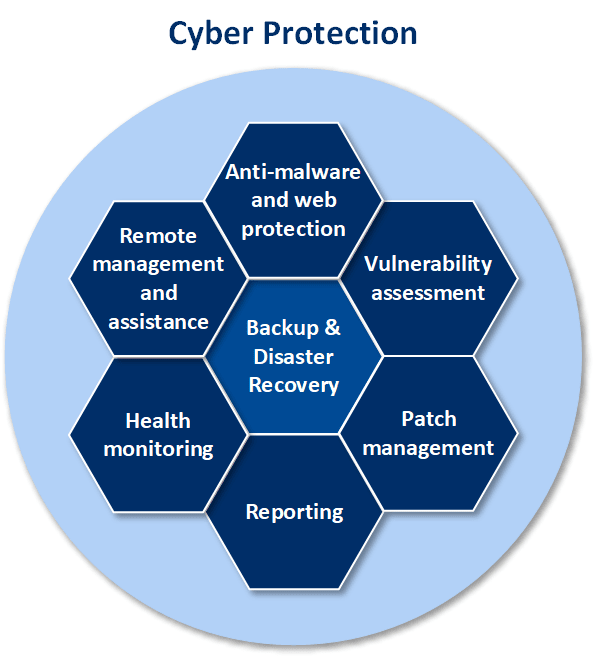
Cyber Protection provides the following functionality:
- Backup and recovery allows you to back up and recover physical machines, virtual machines, and applications.
- Disaster recovery allows you to protect your local environment from disasters by launching the exact copies of machines in the cloud and switching the workload to the cloud servers.
- Antimalware and web protection provides you with the top multi-layered protection based on four different antimalware technologies inside. You will also be able to manage Microsoft Security Essentials and Windows Defender Antivirus from the service console. The URL filtering functionality allows you to prevent malicious file download and block access to suspicious web resources.
- Autodiscovery of machines provides you with an easy and automatic way to register a large number of machines and install a protection agent and additional components.
- Vulnerability assessment allows you to scan Microsoft, Linux, macOS, Microsoft third-party products, and macOS third-party products for vulnerabilities.
- Patch management integrated with backup provides you with the following capabilities: automatic and manual patch approval, scheduled and on-demand patch installation, flexible reboot and maintenance window options, staged deployment.
- Hard drive health control allows you to track the status of hard disks and prevent their crash. Disk control uses a combination of machine learning and SMART reporting to predict disk failures.
- Remote management and assistance allows you to connect and manage machines remotely.
- #CyberFit Score provides you with a security assessment and scoring mechanism that evaluates the security posture of your machine.
- Device control enables you to limit the user access to local and redirected peripheral devices, ports, and clipboard on machines under protection plans.
Why Cyber Protection is special
Cyber Protection has the following unique features:
- Backup scanning in non-endpoint environments that ensures malware-free restores. It increases the potential of rootkits and bootkits detection and reduces loads on your machines.
- Safe recovery based on integrated antimalware scanning and malware deletion to prevent recurrence of an infection.
- Smart protection built on the basis of alarms received from Cyber Protection Operations Center (CPOC). This feature allows you to minimize business process downtime when facing issues like a malware attack, natural disaster, to reduce reaction time, and to avoid data loss.
- Protection from bad patches by creating pre-update backups.
- Continuous data protection that ensures that you will not lose your data changes made between scheduled backups. You can control what will be continuously backed up – Office documents, financial forms, graphic files, and so on. You get improved RPOs due to continuous backups.
- A data protection map that ensures tracking data distribution across the machines, monitoring the protection status of files, and using the collected data as the basis for compliance reports.
- Forensic backup that allows you to collect digital evidence data, include them in a disk-level backup, and use them for future investigations.
- Company-wide allowlist built on backups that allows you to prevent false detections. This feature eliminates time-consuming manual listing of trusted corporate applications, ensures greater productivity, and improves the detection rate by using improved heuristics.
